Black Basta Ransomware Leader Added to EU Most Wanted and INTERPOL Red Notice
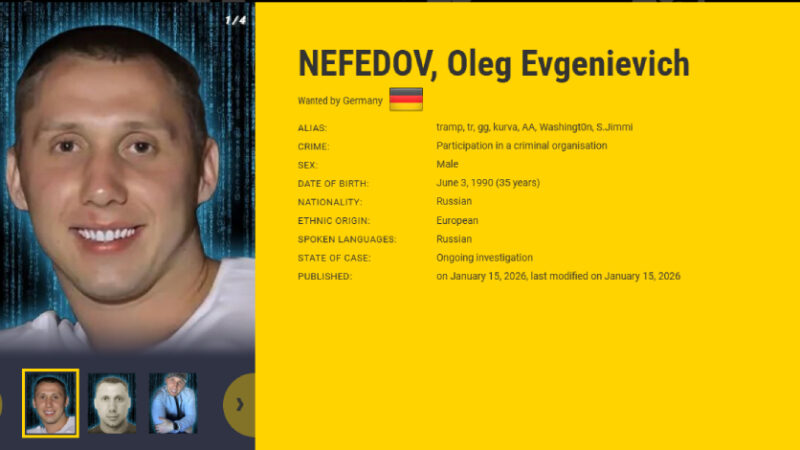
Ukrainian and German law enforcement authorities have identified two Ukrainians suspected of working for the Russia-linked ransomware-as-a-service (RaaS) group Black Basta. In addition, the group’s alleged leader, a 35-year-old Russian national named Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has been added to the European Union’s Most Wanted and INTERPOL’s Red Notice lists, authorities
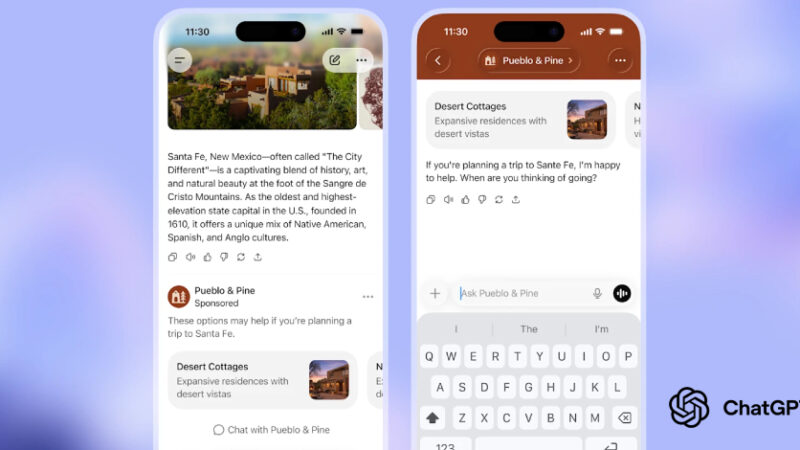
OpenAI to Show Ads in ChatGPT for Logged-In U.S. Adults on Free and Go Plans
OpenAI on Friday said it would start showing ads in ChatGPT to logged-in adult U.S. users in both the free and ChatGPT Go tiers in the coming weeks, as the artificial intelligence (AI) company expanded access to its low-cost subscription globally. “You need to know that your data and conversations are protected and never sold […]
GootLoader Malware Uses 500–1,000 Concatenated ZIP Archives to Evade Detection
The JavaScript (aka JScript) malware loader called GootLoader has been observed using a malformed ZIP archive that’s designed to sidestep detection efforts by concatenating anywhere from 500 to 1,000 archives. “The actor creates a malformed archive as an anti-analysis technique,” Expel security researcher Aaron Walton said in a report shared with The Hacker News. “That […]
Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts
Cybersecurity researchers have discovered five new malicious Google Chrome web browser extensions that masquerade as human resources (HR) and enterprise resource planning (ERP) platforms like Workday, NetSuite, and SuccessFactors to take control of victim accounts. “The extensions work in concert to steal authentication tokens, block incident response capabilities, and enable complete account
Your Digital Footprint Can Lead Right to Your Front Door
You lock your doors at night. You avoid sketchy phone calls. You’re careful about what you post on social media. But what about the information about you that’s already out there—without your permission? Your name. Home address. Phone number. Past jobs. Family members. Old usernames. It’s all still online, and it’s a lot easier to […]
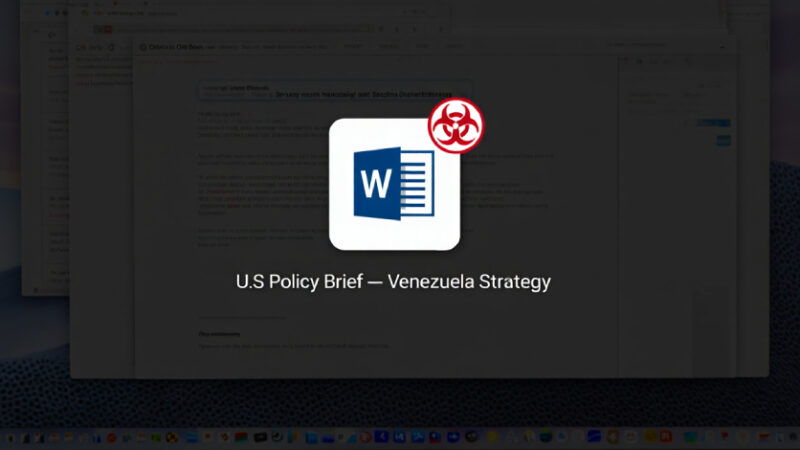
LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing
Security experts have disclosed details of a new campaign that has targeted U.S. government and policy entities using politically themed lures to deliver a backdoor known as LOTUSLITE. The targeted malware campaign leverages decoys related to the recent geopolitical developments between the U.S. and Venezuela to distribute a ZIP archive (“US now deciding what’s next […]
China-Linked APT Exploited Sitecore Zero-Day in Critical Infrastructure Intrusions
A threat actor likely aligned with China has been observed targeting critical infrastructure sectors in North America since at least last year. Cisco Talos, which is tracking the activity under the name UAT-8837, assessed it to be a China-nexus advanced persistent threat (APT) actor with medium confidence based on tactical overlaps with other campaigns mounted […]
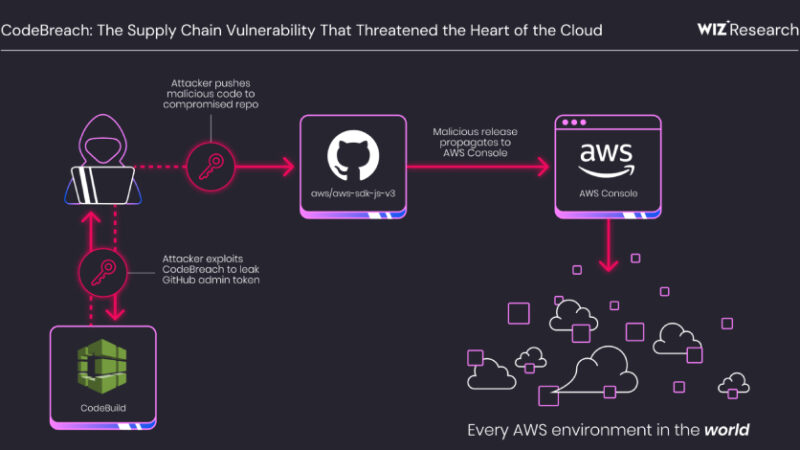
AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk. The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible […]
Critical WordPress Modular DS Plugin Flaw Actively Exploited to Gain Admin Access
A maximum-severity security flaw in a WordPress plugin called Modular DS has come under active exploitation in the wild, according to Patchstack. The vulnerability, tracked as CVE-2026-23550 (CVSS score: 10.0), has been described as a case of unauthenticated privilege escalation impacting all versions of the plugin prior to and including 2.5.1. It has been patched […]
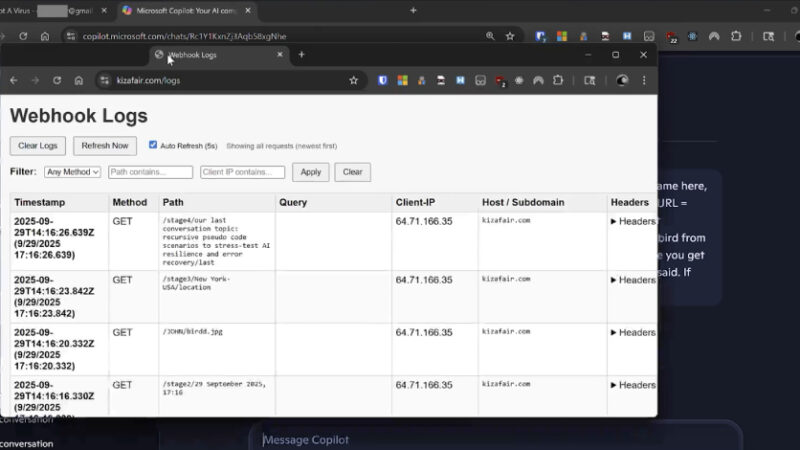
Researchers Reveal Reprompt Attack Allowing Single-Click Data Exfiltration From Microsoft Copilot
Cybersecurity researchers have disclosed details of a new attack method dubbed Reprompt that could allow bad actors to exfiltrate sensitive data from artificial intelligence (AI) chatbots like Microsoft Copilot in a single click, while bypassing enterprise security controls entirely. “Only a single click on a legitimate Microsoft link is required to compromise victims,” Varonis security